Hello everyone! Welcome to my first post outside of my main introduction post (took some time for me to be able to sit down and write this, due to being busy with both work and uni, however expect some more posts soon!). Here I will be discussing the first solve I ever had in picoGym, being the Verify challenge!
What is picoGym?
For those who don’t know, picoGym is a training tool provided by picoCTF which allow aspiring CTF participants, both new and experienced to practice CTF’s (Capture The Flags) and learn new techniques outside of officially run CTF events. It is a great tool which contains it’s own integrated web terminal, that I am starting to go through in order to learn more about cybersecurity and its related fields. I would highly recommend that you all look into it and give it a try!
What is the challenge, and how do you solve it?
The challenge statement is as follows:
“People keep trying to trick my players with
imitation flags. I want to make sure they get the real thing! I’m going
to provide the SHA-256 hash and a decrypt script to help you know that
my flags are legitimate.”
The challenge essentially provides you with a .zip file which contains ‘checksum.txt’, which contains the sha256 checksum of the file which contains the flag, a shell script called ‘decrypt.sh’ which you are supposed to run on the file that contains the flag to decrypt it, and a directory called ‘files’ which contains a whole series of encrypted files to go through.
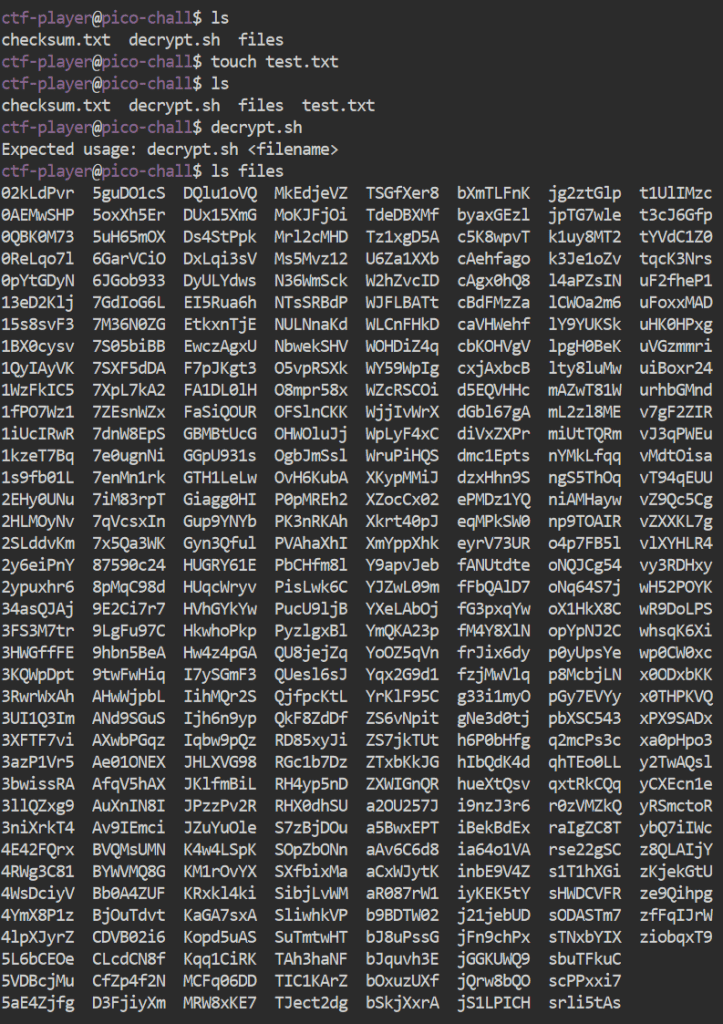
Just a quick note before we continue, I did this via the ssh details that picoGym provides you on the challenge page once you start the instance if you wish to do it in their integrated web terminal (which I would highly recommend using). As you can clearly see, there are way too many files to individually check one-by-one with decrypt.sh, so a more efficient method will need to be utilised. Taking in the knowledge that we were provided with a sha256 checksum, and that if the checksum was the same as one of the files that it would most likely contain the flag, a looping command would be required to check the checksum for each encrypted file, before saving it to a separate .txt file to review after.
I first ran the command “touch sha256sum.txt” to create a .txt file within the root directory to save the results of my command to. To create the loop, I decided to create a “for” loop to select each file in the “files” directory utilising the * wildcard, before running the “sha256sum” command on the encrypted file to calculate it’s checksum before saving it to sha256sum.txt. The command that I devised and its resulting output when I utilised the “cat” command to review the files contents can be seen below: (Note, it isn’t the entire output as it would be too long to show, but you will get the general idea.)
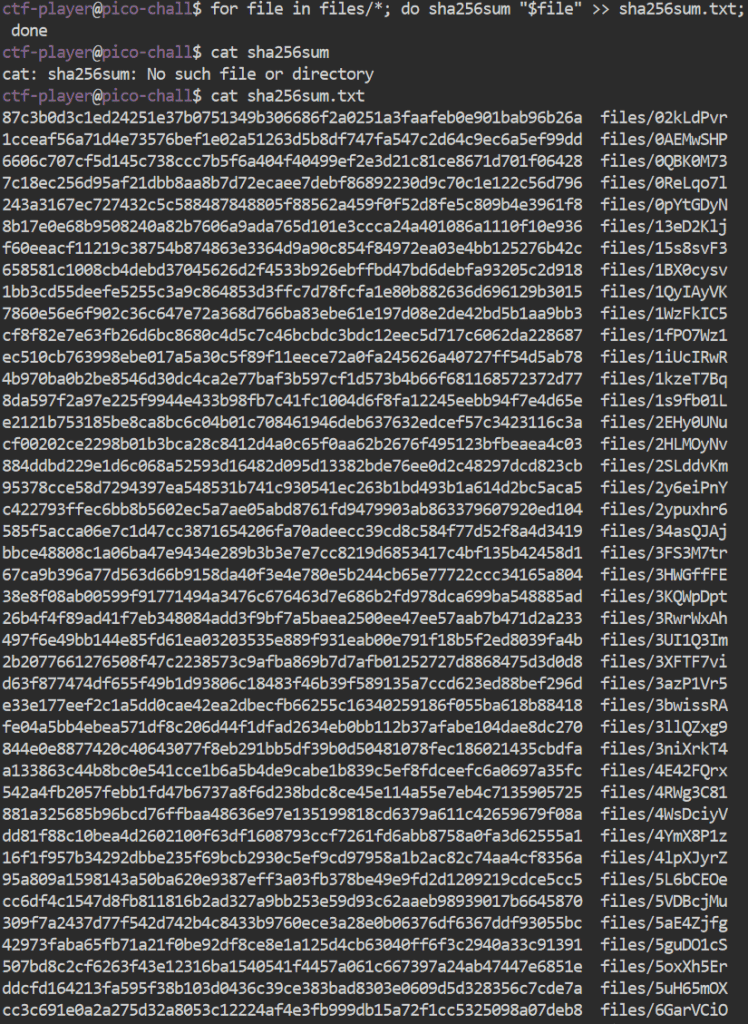
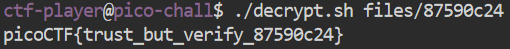
For those who can’t tell, the full command is: “for file in files/*; do sha256sum “$file” >> sha256sum.txt; done”. Once I had all of the checksums and what file they correlated to in the .txt file, I then proceeded to run the following “grep” command which allowed be to search for the specific line that contained the checksum provided to me at the start of the challenge: “grep ‘fba9f49bf22aa7188a155768ab0dfdc1f9b86c47976cd0f7c9003af2e20598f7’ sha256sum.txt”. This returned the output of “fba9f49bf22aa7188a155768ab0dfdc1f9b86c47976cd0f7c9003af2e20598f7 files/87590c24”. As you may have spotted, at the end it proved me with the file that matched the checksum that we were given. From there it was as simple as running the decrypt file on it via “./decrypt.sh files/87590c24” and we had the flag!
Conclusion
At the end of the day, this was my very first CTF challenge that I participated in, and I thoroughly enjoyed it! It served as a perfect introduction to the various commands that are present in the terminal and how to effectively utilise loops to automate various tasks within it. I also believe that if anyone else was to try it out, they would have the exact same wonderful learning experience as me! I have since solved multiple CTF challenges since then, however I will need to go back through them and determine how and what I am going to write up a blog post about. Additionally, I am starting to look into acquiring a Raspberry Pi 5 to start experimenting with a home lab, so stay tuned!